Reversing - I (Unpacking UPX)
Download and rename the file from .txt to .exe
What is unpacking
Below is the simple general overview of a original binary and packed binary. As we can see from the diagram below. The entry point starts at the .text section for non-packed binary where as for the packed binary there contains a packing stub or packer code which is the entry point for the packed binary that keeps the original code compressed.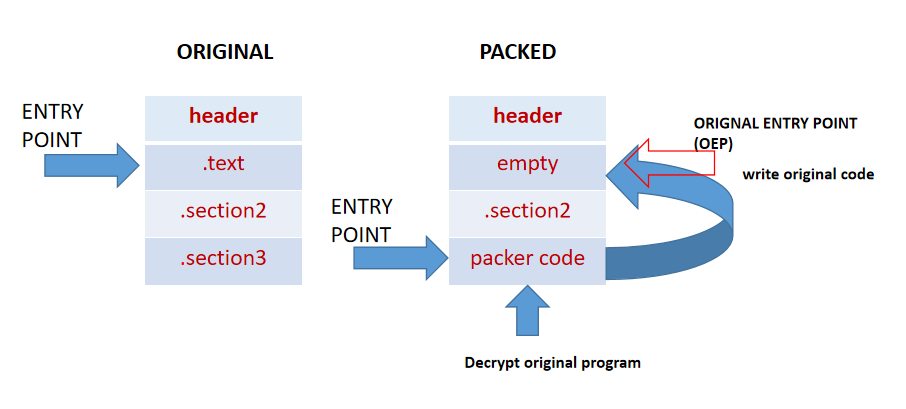
Example: A normal unarchive or unzip folder vs an archive zip folder. In order to see the content or use the content, we need to unzip the content of the file. Similarly for packed binary, in order to see the original code we need to unpacked the zip binary file.
In simple layman terms we can say that unpacking is like unzipping the original data but its only specific to binary executable.
Now that we have a rough idea about what is unpacking lets deep dive into the packed binary
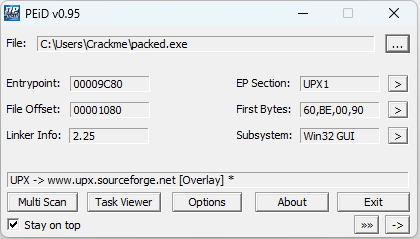
As seen below in PEiD the binary is packed in UPX
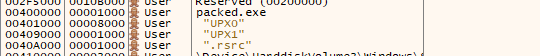
we open the binary file in x32dbg and view the memory map we can see the section and loading address such as UPX0, UPX1 etc.
Now if go to the entry point in the CPU section of x32dbg we will see that there is pushad instruction
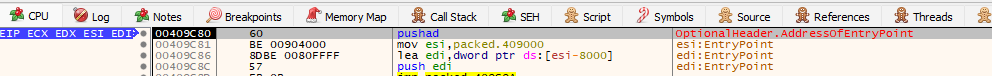
pushad push all the instruction onto the stacks, visit the document to read more about it. pushad
For the reverse operation the popad is being used so that what ever present in the stack can be clear. Since we know that some instruction is being push onto stack which is the packing instruction, so after the popad the packing instruction will be completed and our binary will be unpacked.
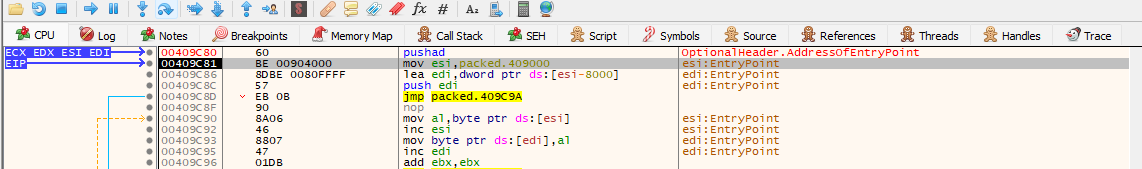
Lets search for popad instruction and set a breakpoint or we can set a breakpoint in the esp register. Clicked f8 on pushad
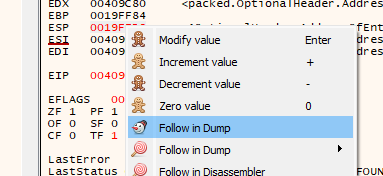
Now go to register esp and right clicked follow dump
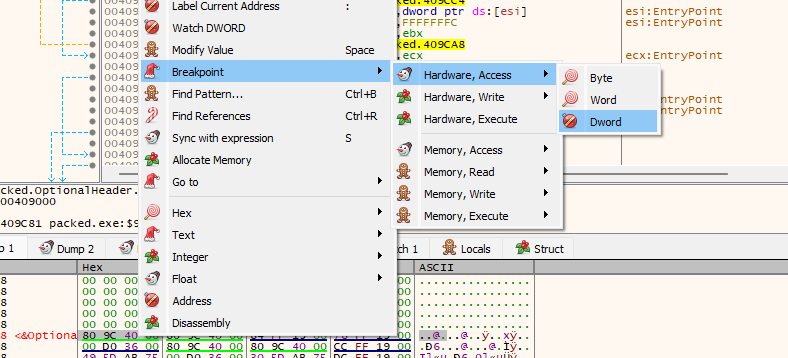
Now on dump select 80 9c 40 00 then set a break point on hardware access Dword
clicked f9 we will see our eip is instruction is after the popad
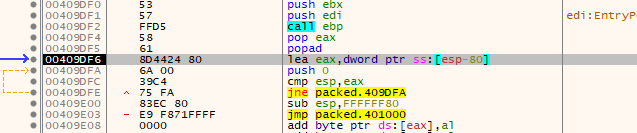
Now find the next jump address to function
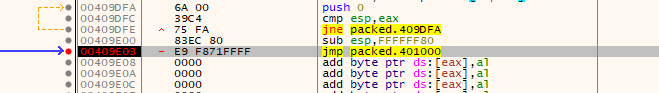
f7 to step in to see the unpacked binary.
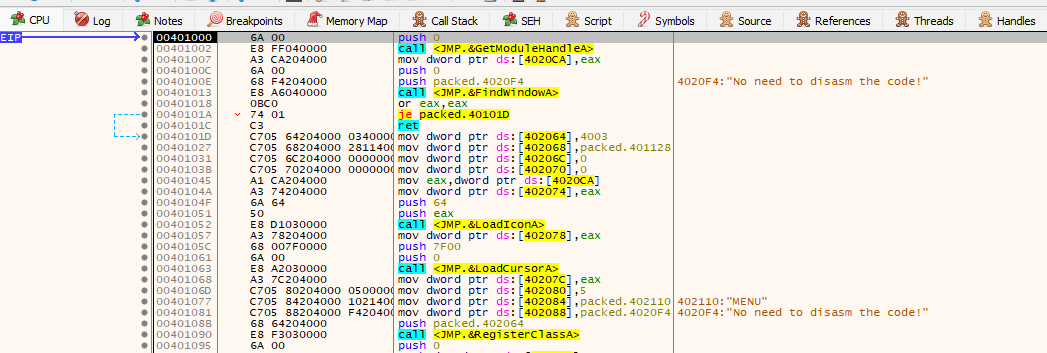
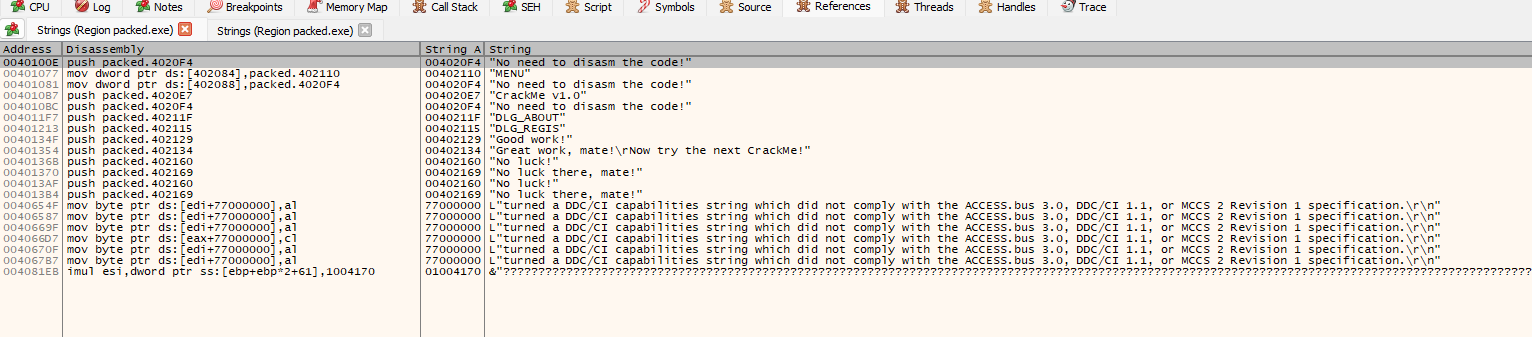
We can see the details by clicking the A2 button to see the strings is being decode or not. If we can see clear strings that there is high indication that the binary is unpacked
Click on Plugin then Scylla or Ctrl + i then IAT Search -> Get Imports then clicked dump the file.
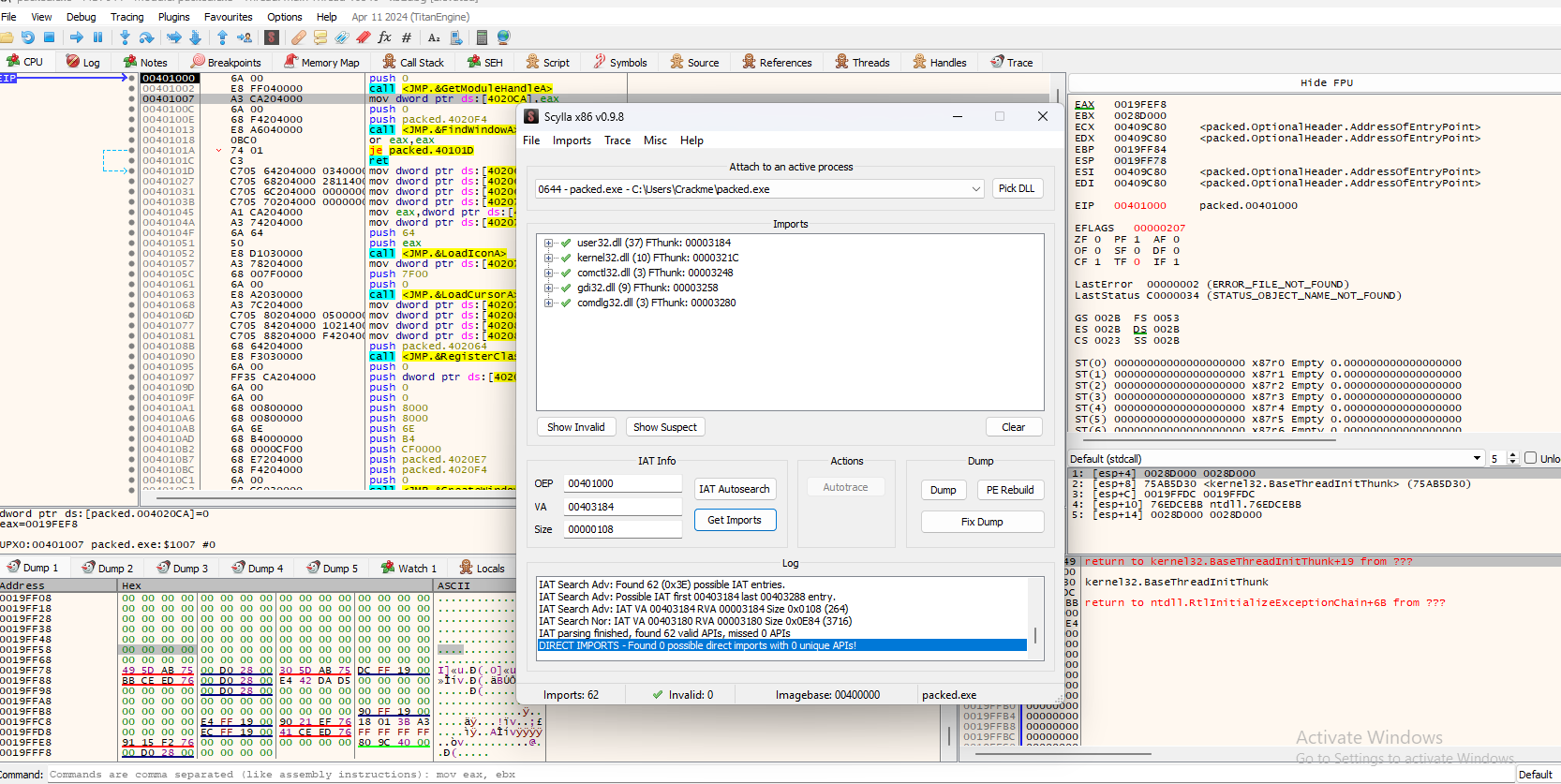
Once the file is dump Fix Dump and clicked the dump file.